При Wardriving идеята е да се засекат wireless мрежи и да бъдат картографирани. Според нашият закон или това което четох това не е нелегално(освен ако не се използват тези мрежи с лоши намерения). Все пак аз съм го направил с цел познание и идеята на тази публикация е да споделя знание.
При Wardriving идеята е да се засекат wireless мрежи и да бъдат картографирани. Според нашият закон или това което четох това не е нелегално(освен ако не се използват тези мрежи с лоши намерения). Все пак аз съм го направил с цел познание и идеята на тази публикация е да споделя знание.
Преди да започнем ще опиша какво ще ни трябва:
Устройства(Gps Reciever с bluetooth, bluetooth на самия лаптоп),
Приложения (gpsdrive,gpsd,bluez-utils,festival,mysql-server,kismet)
След като имаме устройствата ще инсталираме приложенията. Аз лично ползвам Holux 240 slim, но е доста бъгав. От време на време сам решава да се бъгне и да не показа кординатите, а двойчни глупости. За да го върнем в NMEA режим трябва да му извадим батерията с което се връща на първоначални настройки(голямо решение няма що. Има и друго ползвайте друг gps reciever).
Инсталиране на приложенията:
apt-get install gpsdrive gpsd festival mysql-server-5.0 kismet bluez-utils
Сега влючваме нашият GPS Reciever
Изпълняваме "hcitool scan" и виждаме:
Scanning …
00:0B:0D:6D:A1:E8 HOLUX GPSlim240
Ето го и търсеният от нас MAC адрес на Holux Slim 240
Редактираме конф. файлове от bluez-utils в /etc/bluetooth
/etc/bluetooth/hcid.conf
Променяме нашият пин ето тук(в случая е 0000):
passkey "0000"
Сега редактираме /etc/bluetooth/rfcomm.conf
rfcomm0 {
bind no; # Automatically bind the device at startup
device 00:0B:0D:6D:A1:E8; # Bluetooth address of the device
channel 1; # RFCOMM channel for the connection
comment "My GPS device 00:0B:0D:6D:A1:E8"; # Description of the connection
}
Става ясно, че описваме mac адреса на нашият gps reciever
След това вдигаме нашият интерфейс:
hciconfig hci0 up
Свързваме се към нашето устройство Holux:
hcitool cc 00:0B:0D:6D:A1:E8
Отваряме канал
sdptool add --channel=1 OPUSH
и след това биндваме rfcomm0
rfcomm bind rfcomm0 00:0B:0D:6D:A1:E8
За да проверим, че получаваме данните коректно(данните са в текстов вид NMEA) изпълняваме това:
cat /dev/rfcomm0
Ако се вижда нещо от рода:
$GPGGA,235955.065,0000.0000,N,00000.0000,E,0,00,,0.0,M,0.0,M,,0000*4D
$GPRMC,235955.065,V,0000.0000,N,00000.0000,E,,,150406,,,N*7E
$GPVTG,,T,,M,,N,,K,N*2C
$GPGGA,235956.059,0000.0000,N,00000.0000,E,0,00,,0.0,M,0.0,M,,0000*41
$GPRMC,235956.059,V,0000.0000,N,00000.0000,E,,,150406,,,N*72
$GPVTG,,T,,M,,N,,K,N*2C
$GPGGA,235957.059,0000.0000,N,00000.0000,E,0,00,,0.0,M,0.0,M,,0000*40
$GPGSA,A,1,,,,,,,,,,,,,,,*1E
То нашият GPS Reciever още не си е намерил сателитите и трябва да го изчакате известно време(на открито). След като си ги намери тези нули се превръщат в кординати разбира се.
Сега ще стартираме и gpsd които да обработва данните от rfcomm0
gpsd /dev/rfcomm0
Можем да проверим дали правилно приема данните със следната команда:
gpspipe -r
След като пуснахме основните приложения сега ще пуснем и Kismet. Неговата задача е да следи wireless мрежите и да ги записва във файл с техните кординати.
За да стартираме kismet като сървър трябва да укажем source type, а ако не го направим ще ни излезе следната грешка:
FATAL: Please configure at least one packet source. Kismet will not function if no packet sources are defined in kismet.conf or on the command line. Please read the README for more information about configuring Kismet
Това е защото не е зададен capture source type. За целта редактираме /etc/kismet/kismet.conf , ред "source":
source=iwl3945,wlan0,wlan0
Важен е първия аргумент където указваме какъв модул се зарежда за wireless картата, а в този случай е iwl3945
Сега ще накараме Kismet да логва всички wireless мрежи които намери + техните координати. За целта трябва да редактираме /etc/kismet/kismet.conf
waypoints=true
# GPSDrive waypoint file. This WILL be truncated.
waypointdata=~/.gpsdrive/way.txt
Следващата стъпка е да накараме Kismet освен да логва и да говори.
Сега ще направим един малък тест на festival
echo "Hi from mpetrov.net -- Festival test"|festival --tts
Ако ви изплюе следната грешка "Linux: can't open /dev/dsp" то тогава извършете това по- долу:
Решение на проблема по- горе:
Редактира се файл (.festivalrc) или (/usr/share/festival/festival.scm):
vim ~/.festivalrc
и се добавя това:
(Parameter.set 'Audio_Method 'Audio_Command)
(Parameter.set 'Audio_Command "aplay -q -c 1 -t raw -f s16 -r $SR $FILE")
Сега след като имаме инсталиран и работещ festival ще направим промени в конфигурационния файл на kismet.
kismet.conf(за сървъра)
#Променя се от false на true
Speech=true
#Променя се от nato на speech
speech_type=speech
Ако не искаме да говори kismet сървъра, а нашият kismet клиент правим същите промени, но за "kismet_ui.conf"
Сега ще стартираме и gpsdrive. Неговата цел е да взима данните от Kismet ~/.gpsdrive/way.txt , да ги записва в MySQL базата(която ще създадем след малко) и да визуализира текущото ни местоположение на картата.
Първо трябва да създадем нашата база с таблиците които ще ползва gpsdrive изпълняваме:
geoinfo --create-db geoinfo --db-name geoinfo --db-user gast --db-password gast
Стартираме gpsdrive и какво ? Данните се записват и всичко е страхотно :)
Но на мен лично тази карта не ми допада особено и искам всичко това да го преместя в/у картата на GoogleEarth. За целта използвах едно готово python скриптче, което не работеше (нямаше и автор) и трябваше да пренапиша. Може да бъде изтеглено от тук: gpsdriveToGoogleEarth_mpetrov_net.py
изпълняваме python скриптчето което трябва да конвертира от gpsdrive към GoogleEarth:
python gpsdriveToGoogleEarth_mpetrov_net.py
Получавам следната грешка"
#:/tmp# python gpsdriveToGoogleEarth_mpetrov_net.py
Traceback (most recent call last):
File "gpsdriveToGoogleEarth_mpetrov_net.py", line 1, in <module>
import MySQLdb
ImportError: No module named MySQLdb
Това е защото очевидно нямам mysql модул за python. Сега ще го инсталирам:
apt-get install python-mysqldb
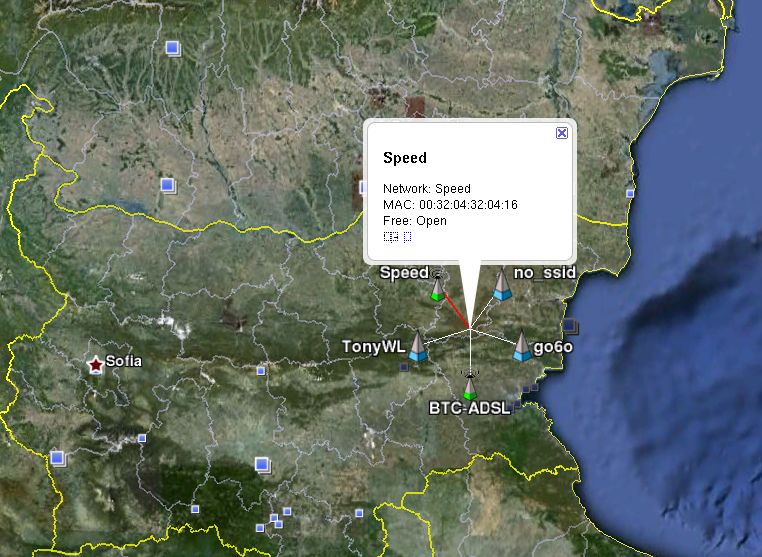
Сега като го изпълним и ще се генерира файл wireless_mpetrov_net.kml които ще вкараме в Google Earth, чрез импорт. Виждаме мрежите които сме картографирали по- рано.
В интерес на истината написах едно простичко bash скриптче което прави някои неща автоматизирано. То може да бъде изтеглено от тук: War Driver 1.0
Потенциален проблем които може да възникне при употребата на Kismet
Проблем при стартиране на Kismet:
ERROR: Unable to find room for logging files within 100 counts. If you really are
logging this many times in 1 day, change log title or edit the source.
WARNING: Error disabling monitor mode: Failed to set channel 0 22:Invalid argument
WARNING: wlan0 (wlan0) left in an unknown state. You may need to manually
restart or reconfigure it for normal operation.
WARNING: Sometimes cards don't always come out of monitor mode
cleanly. If your card is not fully working, you may need to
restart or reconfigure it for normal operation.
Trying to wake networkmanager back up…
Kismet exiting.
Решението е :
rm -fr /var/log/kismet/*
Идеята на тази публикация е с учебна цел. Аз като автор не нося никаква отговорност за причинени от нея щети.
PS: Моля слагайте си WPA2 пароли с максимална дължина и сложност поне като минимално нещо което трябва да направите за свойте wireless мрежи.